## 内存取证 ### 题目 由于管理员的误操作使某机器的内存镜像不慎泄露出去。请选手协助数据安全工程师进行内存取证分析,从泄露的内存镜像中找到登录该机器的密码和泄露的个人敏感信息。 ### flag-1 请找到air账户的登录密码 ```bash volatility.exe -f data.raw --profile=Win7SP1x64 hashdump ``` 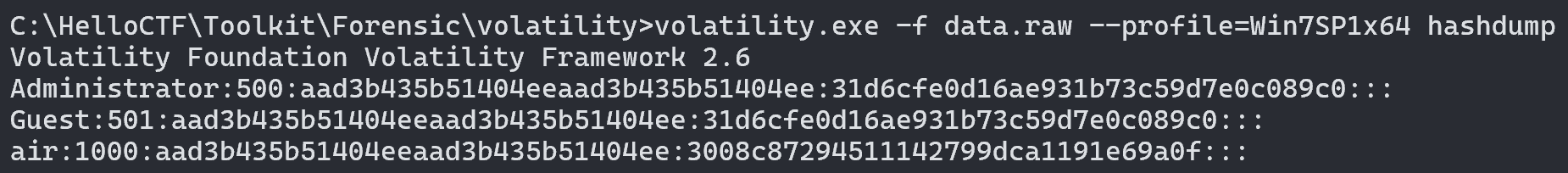 抓到air账户的NTLM hash,对应的明文为 admin123,NTLM对应的明文可在以下这个网站查询 [https://crackstation.net/](https://crackstation.net/) ### flag-2 请找到泄露的个人敏感信息中“张三”的身份证号 从内存中搜索可能后缀的文件,发现存在`xinxi.zip` ```batch volatility.exe -f data.raw --profile=Win7SP1x64 filescan | grep -E "zip|rar|txt|xls|xlsx|doc|docx" ``` 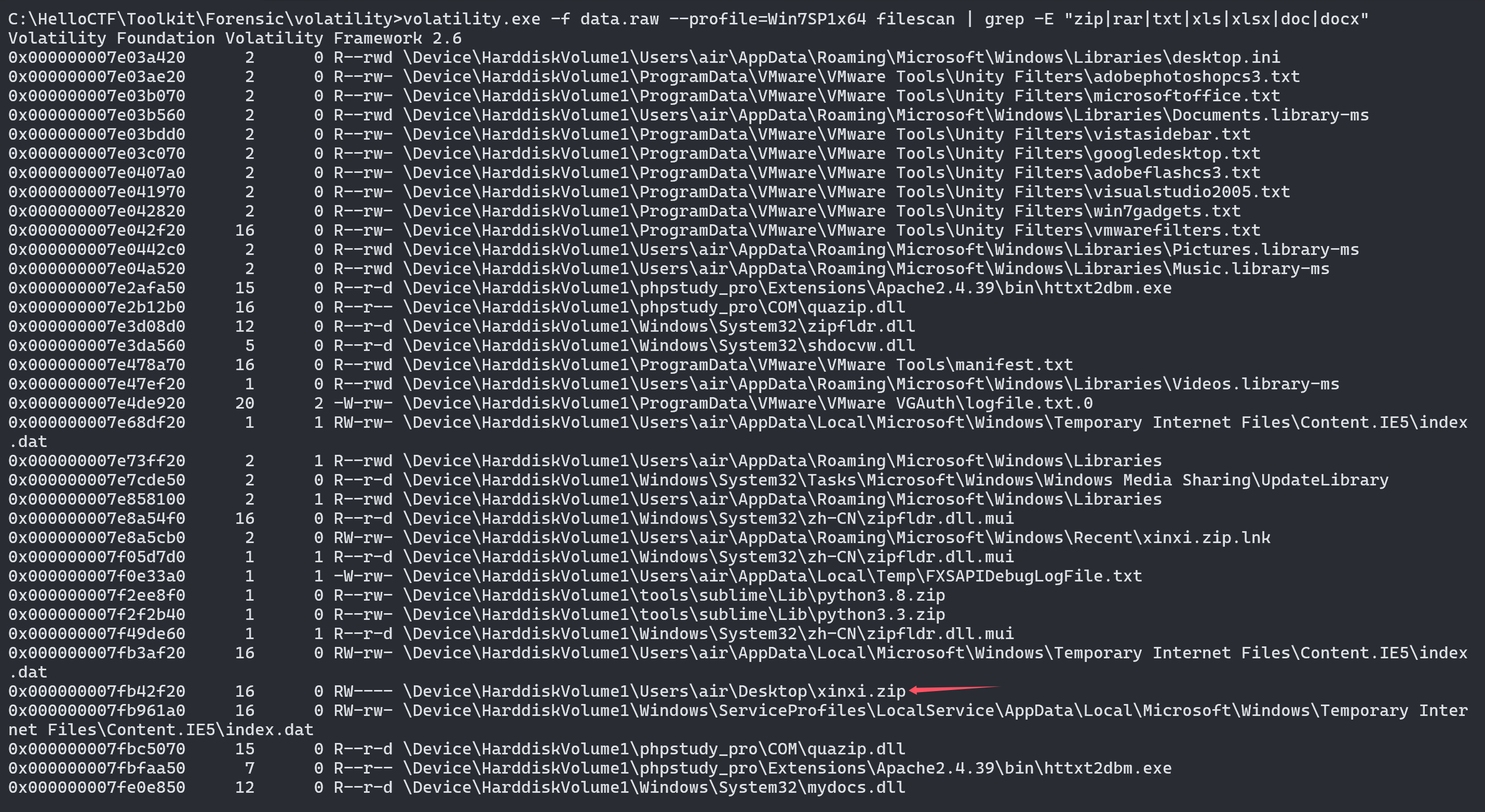 将其提取出来 ```batch volatility.exe -f data.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007fb42f20 -D ./ ``` 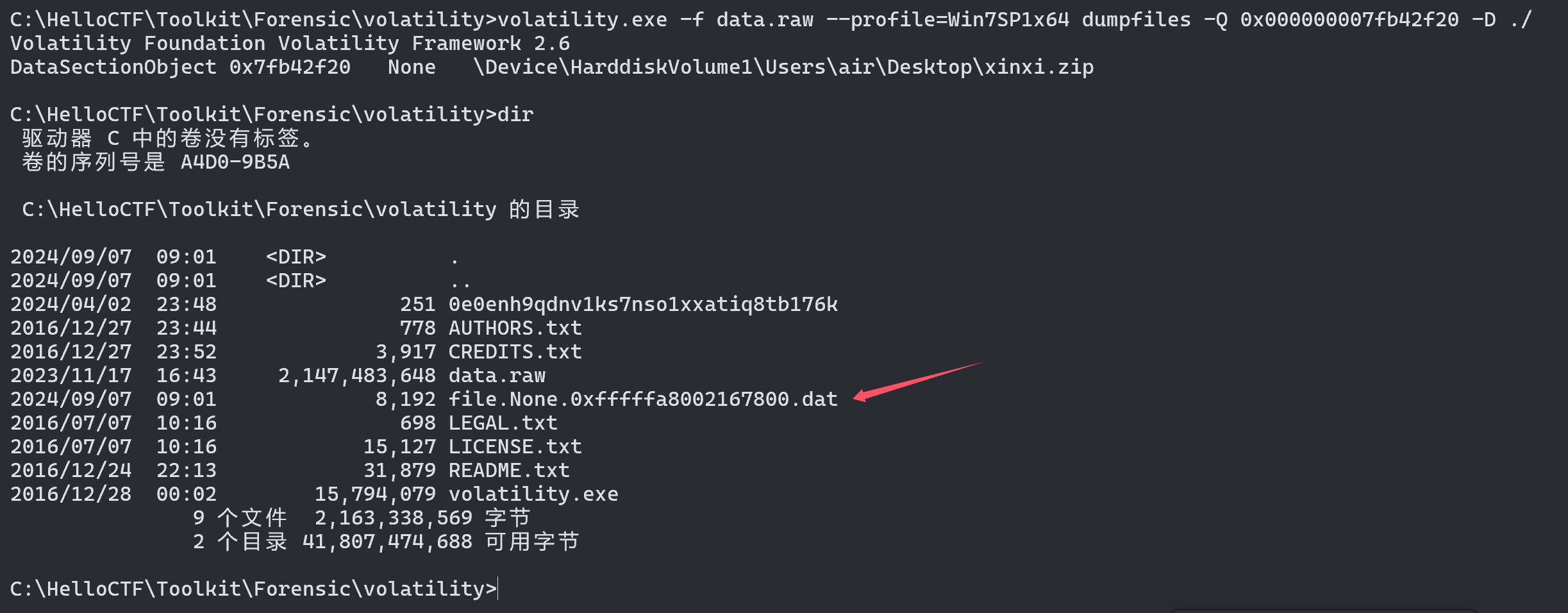 提取出来的文件后缀为`.dat`,手动更改为xinxi.zip即可 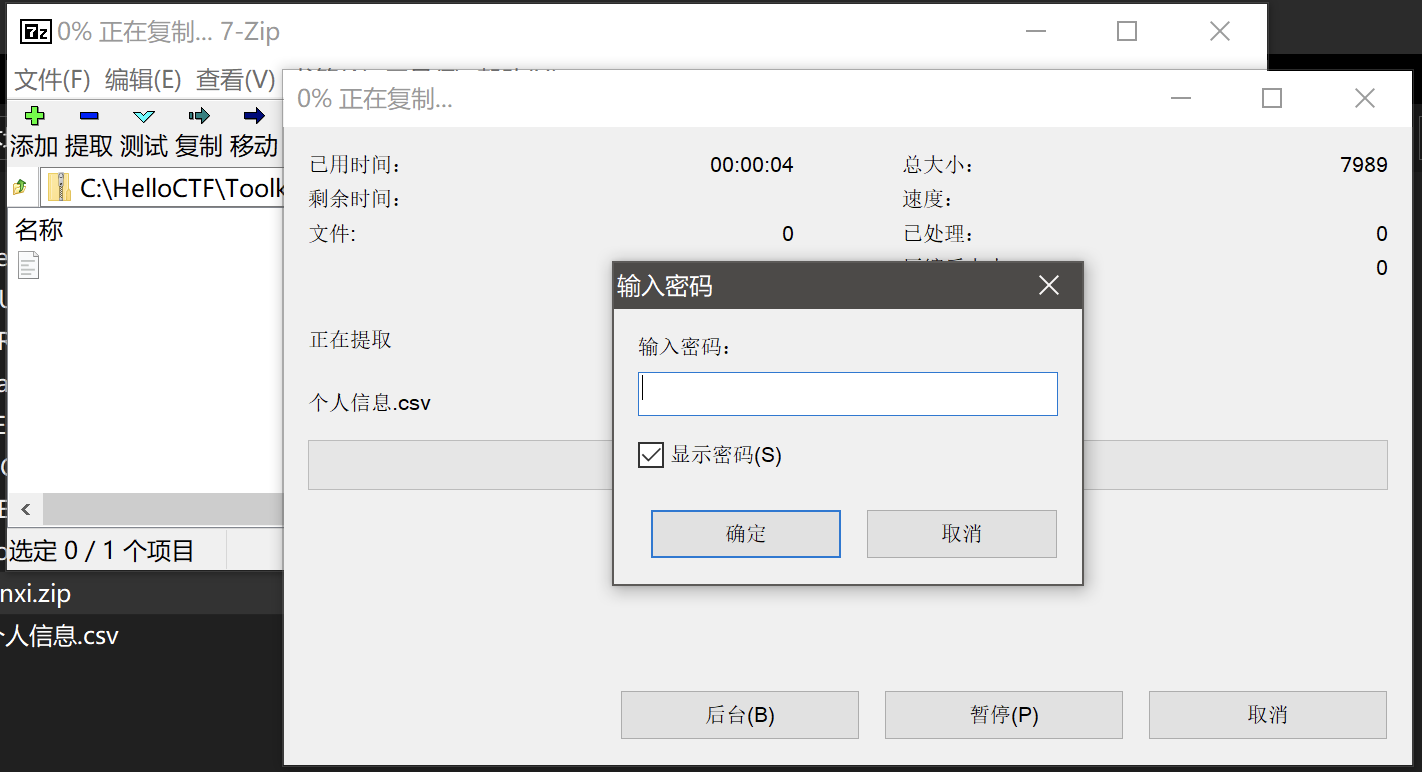 解压发现存在压缩密码,尝试从内存中获取,一般压缩密码会被复制存在于剪贴板中 ```batch volatility.exe -f data.raw --profile=Win7SP1x64 clipboard ``` 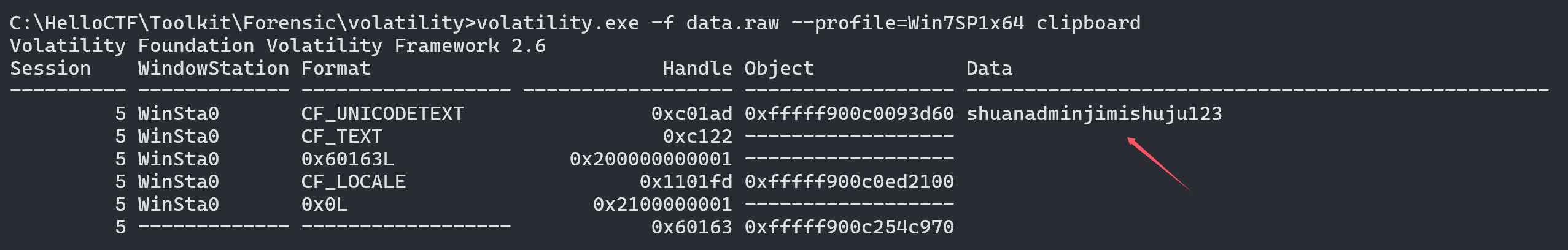 使用`shuanadminjimishuju123`解压得到`个人信息.csv`,拿到张三的身份证号 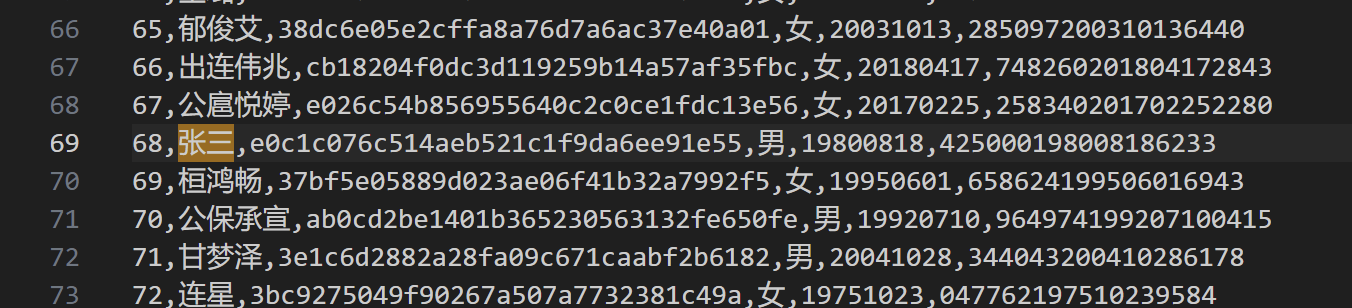 ## 机密图片恢复 ### 题目 某管理员误操作对某机密图片进行了粉碎处理,请选手协助分析,恢复出机密图片内容。 ### flag 打开附件发现为600张被切割开的图片  打开属性,发现都是40\*40像素的图片 使用montage对其进行拼接,得到一张完整的图片 ```bash montage *.png -tile 40x40 -geometry +0+0 flag.png ```  使用gaps对其进行恢复(可能比较耗时 ```bash gaps run ./flag.png f.png --generations=40 --population=600 ```  ## 机密内容恢复 ### 题目 你所在的单位遭到了黑客的勒索病毒攻击,大部分机密文件均被加密,目前应急部门已经完成了对病毒的逆向分析,还原了部分病毒代码,现需要你根据已有的信息分析加密算法,并解密被加密的文件 ### flag 将附件中`keystore.txt`的Y值带入计算key的脚本 ```python from sage.all import QQ from sage.all import ZZ from sage.all import matrix from sage.all import vector def attack(y, k, s, m, a, c): diff_bit_length = k - s delta = c % m y = vector(ZZ, y) for i in range(len(y)): y[i] = (y[i] << diff_bit_length) - delta delta = (a * delta + c) % m B = matrix(ZZ, len(y), len(y)) B[0, 0] = m for i in range(1, len(y)): B[i, 0] = a ** i B[i, i] = -1 B = B.LLL() b = B * y for i in range(len(b)): b[i] = round(QQ(b[i]) / m) * m - b[i] delta = c % m x = list(B.solve_right(b)) for i, state in enumerate(x): x[i] = int(y[i] + state + delta) delta = (a * delta + c) % m return x Y=[3312417817] k = 128 s = 32 m = 297962456582253955990046250846979218011 a = 71211951805712323543315295789950870568 b = 215968094306987982220961475017392133478 X = attack(Y[:40],k,s,m,a,b) print(X[0]) ``` sage脚本可在线执行 [ Sage Cell Server A simple, embeddable interface for SageMath https://sagecell.sagemath.org/](https://sagecell.sagemath.org/ " Sage Cell Server A simple, embeddable interface for SageMath https://sagecell.sagemath.org/")  算出key后,将key替换入解密脚本 ```python key = 126467822674263562126638546968939989865 from Crypto.Util.number import * import random class YSenc: def __init__(self,key) -> None: self.shift = 128-32 self.m = 297962456582253955990046250846979218011 self.a = 71211951805712323543315295789950870568 self.b = 215968094306987982220961475017392133478 self.x = key def _next(self): self.x = (self.a*self.x + self.b) % self.m def kx(self,n): Y = [] X = [] kx = b"" while len(kx) < n: Y.append(self.x >> self.shift) X.append(self.x) kx += self.x.to_bytes(16,"big") self._next() f = open("output.txt","w") f.write(f"Y={Y}\nX={X}") return kx def encrypt(self,plaintext): return bytes(x ^ y for x, y in zip(plaintext, self.kx(len(plaintext)))) with open(r"secret_credentials.csv.lock","rb") as f: data = f.read() with open(r"secret_credentials.csv","wb") as f: f.write(YSenc(key).encrypt(data)) ``` 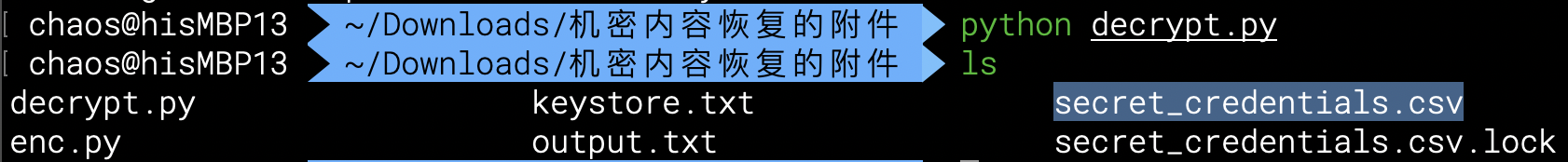 拿到flag 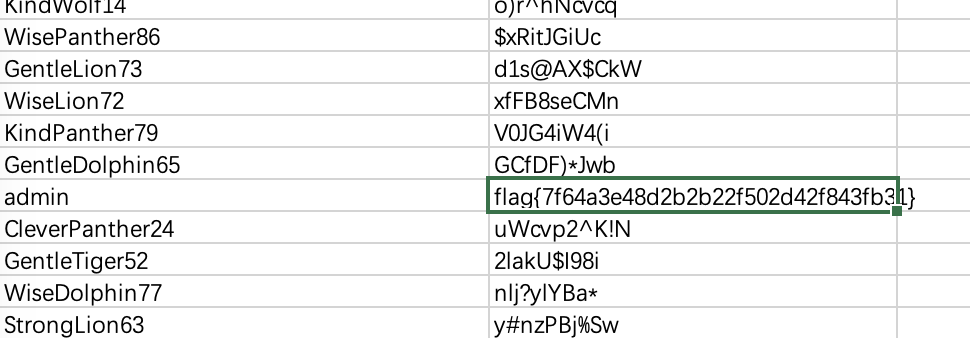 Loading... ## 内存取证 ### 题目 由于管理员的误操作使某机器的内存镜像不慎泄露出去。请选手协助数据安全工程师进行内存取证分析,从泄露的内存镜像中找到登录该机器的密码和泄露的个人敏感信息。 ### flag-1 请找到air账户的登录密码 ```bash volatility.exe -f data.raw --profile=Win7SP1x64 hashdump ```  抓到air账户的NTLM hash,对应的明文为 admin123,NTLM对应的明文可在以下这个网站查询 [https://crackstation.net/](https://crackstation.net/) ### flag-2 请找到泄露的个人敏感信息中“张三”的身份证号 从内存中搜索可能后缀的文件,发现存在`xinxi.zip` ```batch volatility.exe -f data.raw --profile=Win7SP1x64 filescan | grep -E "zip|rar|txt|xls|xlsx|doc|docx" ```  将其提取出来 ```batch volatility.exe -f data.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000007fb42f20 -D ./ ```  提取出来的文件后缀为`.dat`,手动更改为xinxi.zip即可  解压发现存在压缩密码,尝试从内存中获取,一般压缩密码会被复制存在于剪贴板中 ```batch volatility.exe -f data.raw --profile=Win7SP1x64 clipboard ```  使用`shuanadminjimishuju123`解压得到`个人信息.csv`,拿到张三的身份证号  ## 机密图片恢复 ### 题目 某管理员误操作对某机密图片进行了粉碎处理,请选手协助分析,恢复出机密图片内容。 ### flag 打开附件发现为600张被切割开的图片  打开属性,发现都是40\*40像素的图片 使用montage对其进行拼接,得到一张完整的图片 ```bash montage *.png -tile 40x40 -geometry +0+0 flag.png ```  使用gaps对其进行恢复(可能比较耗时 ```bash gaps run ./flag.png f.png --generations=40 --population=600 ```  ## 机密内容恢复 ### 题目 你所在的单位遭到了黑客的勒索病毒攻击,大部分机密文件均被加密,目前应急部门已经完成了对病毒的逆向分析,还原了部分病毒代码,现需要你根据已有的信息分析加密算法,并解密被加密的文件 ### flag 将附件中`keystore.txt`的Y值带入计算key的脚本 ```python from sage.all import QQ from sage.all import ZZ from sage.all import matrix from sage.all import vector def attack(y, k, s, m, a, c): diff_bit_length = k - s delta = c % m y = vector(ZZ, y) for i in range(len(y)): y[i] = (y[i] << diff_bit_length) - delta delta = (a * delta + c) % m B = matrix(ZZ, len(y), len(y)) B[0, 0] = m for i in range(1, len(y)): B[i, 0] = a ** i B[i, i] = -1 B = B.LLL() b = B * y for i in range(len(b)): b[i] = round(QQ(b[i]) / m) * m - b[i] delta = c % m x = list(B.solve_right(b)) for i, state in enumerate(x): x[i] = int(y[i] + state + delta) delta = (a * delta + c) % m return x Y=[3312417817] k = 128 s = 32 m = 297962456582253955990046250846979218011 a = 71211951805712323543315295789950870568 b = 215968094306987982220961475017392133478 X = attack(Y[:40],k,s,m,a,b) print(X[0]) ``` sage脚本可在线执行 [ Sage Cell Server A simple, embeddable interface for SageMath https://sagecell.sagemath.org/](https://sagecell.sagemath.org/ " Sage Cell Server A simple, embeddable interface for SageMath https://sagecell.sagemath.org/")  算出key后,将key替换入解密脚本 ```python key = 126467822674263562126638546968939989865 from Crypto.Util.number import * import random class YSenc: def __init__(self,key) -> None: self.shift = 128-32 self.m = 297962456582253955990046250846979218011 self.a = 71211951805712323543315295789950870568 self.b = 215968094306987982220961475017392133478 self.x = key def _next(self): self.x = (self.a*self.x + self.b) % self.m def kx(self,n): Y = [] X = [] kx = b"" while len(kx) < n: Y.append(self.x >> self.shift) X.append(self.x) kx += self.x.to_bytes(16,"big") self._next() f = open("output.txt","w") f.write(f"Y={Y}\nX={X}") return kx def encrypt(self,plaintext): return bytes(x ^ y for x, y in zip(plaintext, self.kx(len(plaintext)))) with open(r"secret_credentials.csv.lock","rb") as f: data = f.read() with open(r"secret_credentials.csv","wb") as f: f.write(YSenc(key).encrypt(data)) ```  拿到flag  最后修改:2025 年 11 月 28 日 © 允许规范转载 赞 如果觉得我的文章对你有用,请随意赞赏